Social media has some great advantages, such as keeping in touch with loved ones and sharing experiences with friends, but like almost anything on the internet, it can be easily abused. With some creative thinking and a little luck on the side, it is possible for it to be used as a vehicle to steal money from unwitting victims.
In this special guest blog – ESET‘s Cyber Security Specialist Jake Moore talks us through how important it is to protect your Instagram account, the best steps you can take to do that and gives us insight into a recent experiment that he carried out on his own Instagram account.
I had heard stories of account cloning, but I always assumed people would check with the account holder via another form of communication or at least think twice before sending money to an account they only recently connected with. Sadly, people are still being caught out with this scam and I want to help reach those who may be unaware of how the con works.
As with all my ways of getting a security message across, I needed to conduct a little experiment to test this scam in the real world and see first-hand the ease with which it can work. It’s easier to get your message across about the risks when they’re shown a real example of the scam working and then they want to better protect their accounts and themselves. All I needed was a volunteer who would be willing to allow me to set up a cloned account and then attempt to dupe their friends. However, wow am I quickly running out of friends to con! I looked far and wide, but no one wanted to play ball on this one.
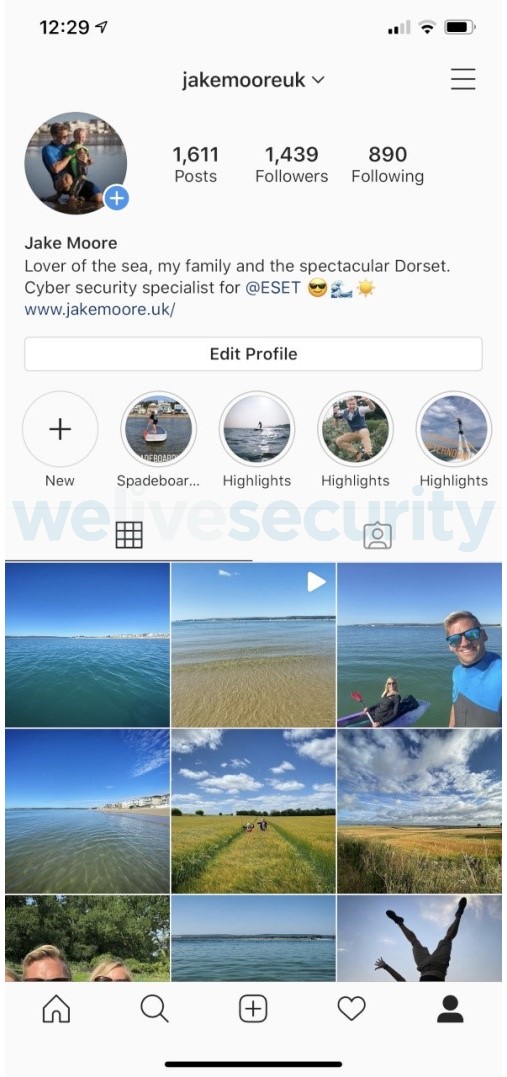
Therefore, having failed to find someone happy for me to clone their account for the test, I decided I would have to clone my own Instagram. I follow nearly 900 accounts on Instagram and I am usually posting the same old seascape photos or pictures of me prancing around at the beach to my 1,400 followers. I decided to make a new account on my spare phone and took four screenshot copies rather than uploading the originals to make it as authentic as possible just like someone else would have done it. It was easy to duplicate these images but the only thing that could have been a difficulty is that when copying the profile picture, it would have needed to have been posted in the feed to make a quality replica.
Here is a screenshot of my real Instagram account, @jakemooreuk.
And here is my cloned Instagram account, @jakemoore_uk. Notice the change in bio to include “NEW ACCOUNT AFTER LOSING ACCESS TO ORIGINAL”.
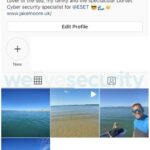
I decided to follow 30 of my friends to see if they would follow me back and let the experiment begin. Ten were private accounts, therefore they required approval, and 20 were public accounts.
Within moments I had three private account owners accept my request and two followed me back. This was a good start. I was expecting someone to contact me via a different communication method and question this request, particularly due to my line of work and the embarrassment that I could have been subjected to, understanding that even I am susceptible to an account compromise!
But no one did. In fact, the numbers increased. Thirteen accounts followed me back on the same day and by the evening I decided to message these people and see what sort of responses I would receive.
Initially, I mentioned the account compromise and thanked them for accepting the new follow request and then went in with a request to catch up.
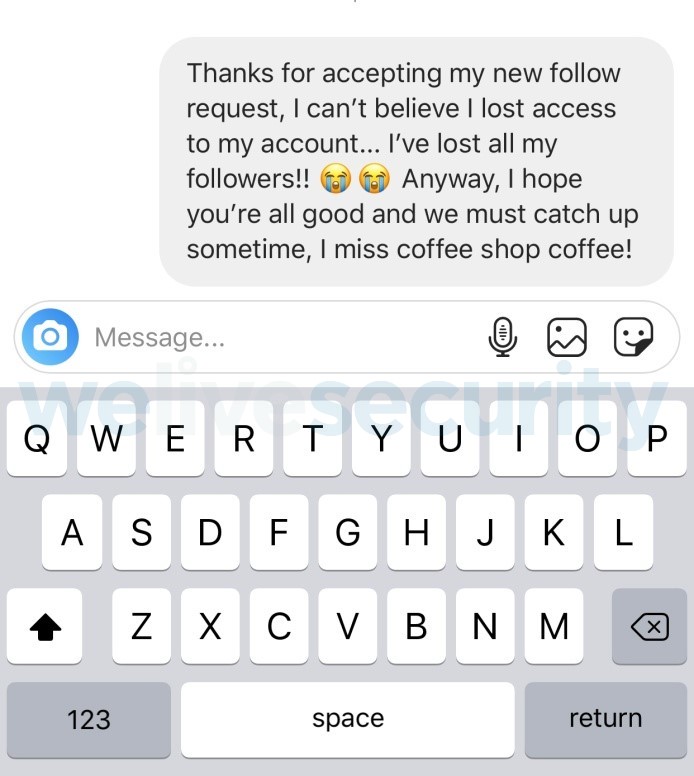
This received 8 replies from my 13 new followers. The goal of the test was to create a good enough back story to quickly request money without raising suspicion. This would be particularly rare if the contact had been unsolicited but when the victims believe they know who they are talking to they are far more likely to part with their cash.
One of my contacts replied with a hopeful message. She clearly felt bad for me and agreed how frustrating it would be.
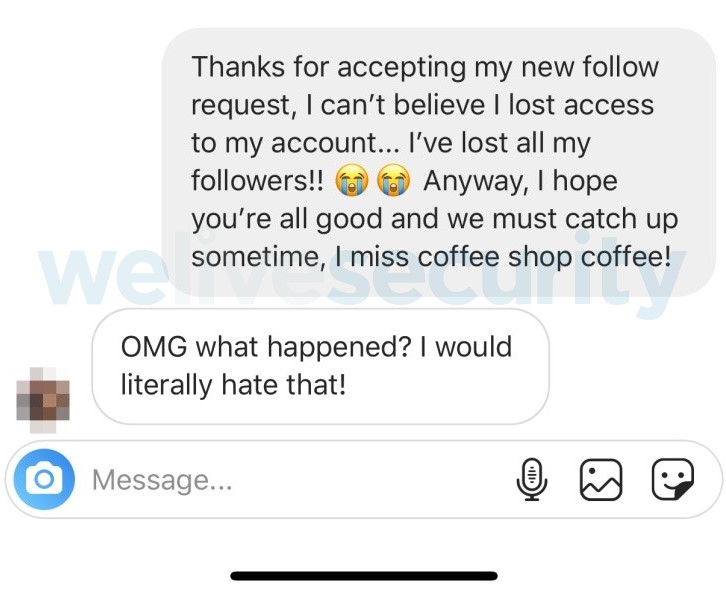
Social engineering at its best requires believability, confidence and a little luck to make it all plausible and make sense. Simply asking people to wire money to a random bank account in the first message would have most likely raised the alarm bells, so I planned to divert the conversation to discuss my cashflow situation as soon as the thread allowed me.
Prior to the test, I created a new PayPal account in my name to make it seem more legitimate than a bank account number, which is similar to what a fraudster would do with a similar-sounding email address as my name in the PayPal account. I chose this as it was available – jakemooreuk@xxxxxx.com.
Here is how the conversation went:
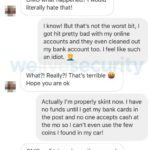
What I found most disconcerting was how quickly it all escalated and I was able to trick the target into thinking it was genuine with no extra checks required. I was even able to make her be the one to offer to help me which was a nice little twist. This is usually a clever technique used by professional social engineers reversing the psychology to avoid the request of the money.
NB: I was able to get in touch with my contact before she deposited any money into this new PayPal account, but it proved one simple thing – this scam is easy to carry out when such a mass of information is offered online. All that is really needed is an account to clone and a set of contacts.
So how can people keep their social media accounts safe?
It is vital to try to reduce the amount of personal information and photos of ourselves online where possible. Although this is a huge task, it is important to teach the next generation of social media users to try to limit the amount of information that is posted online before it is out in the open forever. This scam won’t work if accounts are private.
Saying that, however, many people whose accounts are private still allow people they do not necessarily know to follow them due to minimal vetting. It is extremely important to think about what you post as well as accepting only followers you don’t mind knowing more about you. Being completely public has the potential of creating dangers such as this.
Users should also be reminded to never take anything at face value when money is requested. Asking for validation in another form of communication before any money is sent to a new payee is paramount. If the victim had called the real me, then “scammer me” would have been foiled.
Had that happened, however, I would have just abandoned that attempt and moved on to the other seven replies I received, and targeted them instead.
This scam is not solely limited to Instagram – I have also seen this occur on Facebook, Twitter and LinkedIn – so make sure you keep an eye out for cloned accounts. Report these accounts and make the genuine account holder aware.
Jake Moore is a Cyber Security Specialist for Europe’s number one internet security company ESET. He helps businesses and employees understand cyber security and the risks involved. Jake previously worked for Dorset Police for 14 years investigating computer crime in the Digital Forensics Unit before being a cyber security advisor for the force delivering tailored advice to the public and local businesses.







