Watch out Snapchatters! In this special guest blog – we invite ESET‘s Cyber Security Specialist Jake Moore back for another instalment of how to add more security to your social media accounts. If you’re an avid Snapchatter, then this blog is for you! Jake explains how easy it may be for somebody to hijack your Snapchat account, and alarmingly, all they need to do is peer over your shoulder…
After demonstrating in 2020 the ease with which anybody can hijack your WhatsApp, I took a hiatus in ethically hacking people’s accounts. It’s just not the same hacking your own accounts, lockdowns or not. But now as we slowly start to mix with people again, I thought it would be fun to test out my old tricks on unsuspecting victims – I mean friends – to see if it is still possible in well-known apps. I was shocked at how easy it remains.
I recently looked at the top 10 free apps on the Apple App Store and decided to target one to see if I could take control of someone else’s account. These experiments are not just about highlighting how easily it can be achieved, but also about taking the opportunity to show you the prevention methods available to help secure all your accounts.
Snapchat caught my eye due to its target audience of 18-24-year-olds (although many of its users are thought to be younger). Generation Z are often thought of as “tech savvy”, having been the first generation to grow up with technology from their early years.
On the other hand, they’re also sometimes viewed as those who cut security corners – from not setting up two-factor authentication to sharing passwords with friends. So, I decided to see what the security was like on the app and see if it could be as easily dodged as with WhatsApp.
This time round, I used a technique called “shoulder surfing”, which I like to call “shoulder jacking” and which involves someone looking over your shoulder in order to steal your sensitive information such as passwords, PINs or confirmation codes. This simple and yet effective technique remains a huge problem with social media and other accounts, but could someone use it to hijack your Snapchat account?
The experiment
I haven’t got a Snapchat account but a few of my friends do. I needed an account to test and as expected, I like to ask my colleagues for permission first. My friend, who I will call “Elle”, was indeed interested in my hypothesis, so when I asked her if I could attempt to hack into her Snapchat account, she willingly obliged in the name of cyber-awareness – as long as I didn’t post anything from her account, were I to be successful!
Offering to pay for Elle’s lunch in exchange for my attempt and her generally being a good sport, a few of us went out to lunch in Bournemouth. At the table, I was sat next to Elle and we were both on our phones despite engaging in a conversation. I had previously installed Snapchat on my phone, but had not set up or logged into an account yet. I opened the app on my phone and viewed the following screen to sign in. It has a hacker’s favourite link right there in the middle highlighted “Forgot your password?”.
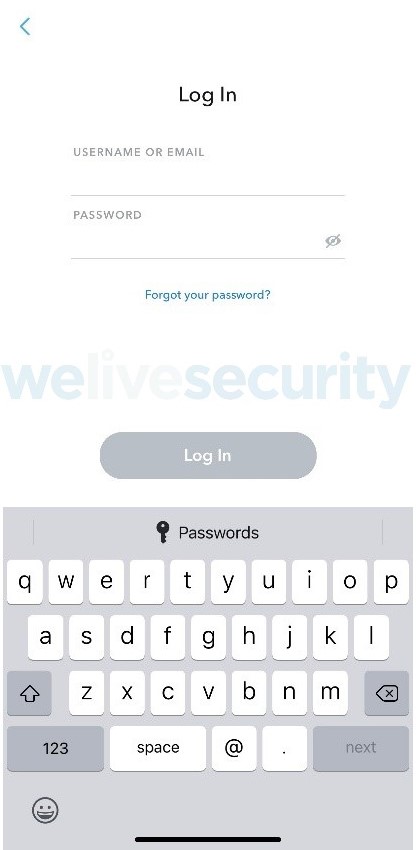
This is often the first port of call for anyone attempting to hijack an account to test the security and possible entry methods. I clicked on “Forgot your password?” and the app asked me to choose how I wanted to reset the password. The options were “via phone or via email”. I chose via phone, to which it then requested my phone number.
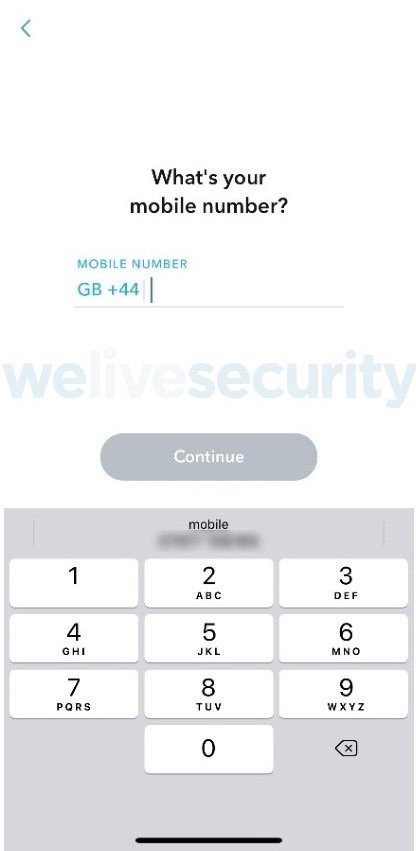
With Elle still on her phone at the table, I proceeded by entering her phone number and then waited eagerly next to her for that moment to “shoulder jack” her confirmation code. As she was looking at her phone in a message conversation, the confirmation code arrived as a drop-down notification at the top of her Apple iPhone screen, and I was able to quickly read the six-digit number and remember it.
I thought at this stage she would have put two and two together, but she just ignored it and carried on with messaging a friend. In fact, when I told her later what I had done, she said she didn’t even notice the message from Snapchat as she gets “so many notifications and they blur into one”.
I input the confirmation code on my phone and I was immediately asked to add a new password that I entered – “JakeIsAwesome.1” seemed like a good choice so she would have to type that in to recover her account later. At this stage, it was as easy as it was to take control of someone’s WhatsApp account in my previous experiment, but Snapchat had one extra layer to fully command control over the account.
Although it didn’t ask for a password (presumably due to being able to create an account without an email and username), this extra security layer was yet another confirmation code sent to her phone number again via text. I wasn’t ready for this having not predicted it, but I was still able to view the SMS message drop into Elle’s notifications again while she was still on it (and oblivious, too). With this code, I gained entry and took full control, even locking her out of the account on her own phone.
I had promised I would not post anything or contact her friends, but my proof of concept had worked. This was easily completed with only knowing her phone number and being able to be within shoulder-surfing distance of her cell phone. Snapchat users need to be aware that their accounts are at risk should someone in their vicinity want to hack them and possibly even hold their accounts to ransom.
Taking this one step further, I believe this attack could even be remotely enabled should a manipulative social engineer choose to call them up and persuade them into handing over the confirmation codes over a voice call. This is something that we are seeing a gradual increase in and people need to err on the side of caution.
Had the only option been to verify the account via email, this experiment would have been near impossible. This would have meant I would have needed Elle to click on the email sent to her and click on the link within the message – two things I presume she would not have done. Snapchat’s password recovery mechanism – using a code sent via an unencrypted messaging service that shows up in the phone’s notification pane – simply opens up an attack vector that is much easier to exploit.
How can you recover your Snapchat account?
Recovering a stolen Snapchat account is, sadly, not always easy. Everything depends on the changes the hacker has made to the account. If the hacker has only changed the password, you can get your account back by following the same steps again shown above.
However, if they have changed the phone number, email address or added two-factor authentication, there are very limited options and like with most social media, it is difficult to communicate with these companies and gain help with undoing such attacks. If you think your account has been compromised, Snapchat has this advice for you.
How can you secure your Snapchat account?
Beyond a strong and unique passphrase (which you should use on all your online accounts), make sure to turn on two-factor authentication within Snapchat’s settings, as well as implement it on all other apps that offer it. In Snapchat, head over to Settings and find the Two-Factor Authentication set up – while it’s okay to use SMS-based 2FA, it’s far better to use an authenticator app such as Microsoft Authenticator or Google Authenticator.

You may not have a Snapchat account, but you may know someone who does. Please make those users aware of the ‘SnapHack’ and urge them to apply this advice on all of their online accounts.
Shoulder surfing as such is best thwarted by preventing anybody from covertly looking at your screen when you enter sensitive information into an app or website, especially in public places. Better still, make sure you turn off notification previews, so that they’re hidden from prying eyes when your phone is locked. Also, be sure to actively monitor your SMS messages when using your phone or tablet around other people – this is also what would have foiled my attack at Elle’s Snapchat account.
Jake Moore is a Cyber Security Specialist for Europe’s number one internet security company ESET. He helps businesses and employees understand cyber security and the risks involved. Jake previously worked for Dorset Police for 14 years investigating computer crime in the Digital Forensics Unit before being a cyber security advisor for the force delivering tailored advice to the public and local businesses.






